With the recommendation of the Cloud Native Computing Foundation to take the step of containerization, Azure App Service will likely not be the number one web hosting option in the cloud even if it CAN run containers. Still, App Service is a mature hosting platform and has an enormous amount of easily configurable options for more efficient and secure solutions. KeyVault References is one of those options, and one, I feel, is not very well known.
The recommended way to access Azure KeyVault from your other Azure services is by using an Azure AD security principal. Most Azure services can register their own principal that represents the service itself, the system managed identity. After enabling it for the App Service the Object ID can be used in services like KeyVault to assign permissions to the identity.
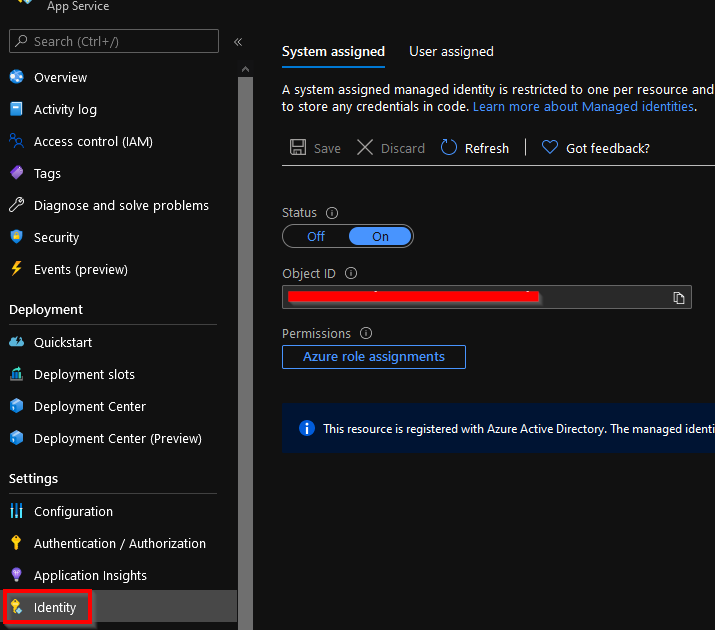
After assigning this principal an access policy (with for example GET permissions on secrets) in KeyVault the identity can be used to authenticate to KeyVault from App Service without using credentials. To access KeyVault secrets from .NET code the SecretClient from the Azure.Security.KeyVault.Secrets Nuget package can be used. When using the SecretClient you just need to do is pass the KeyVault Uri and an instance of DefaultAzureCredential() into the constructor is. The DefaultAzureCredential instance will use the system managed identity to fetch secrets.
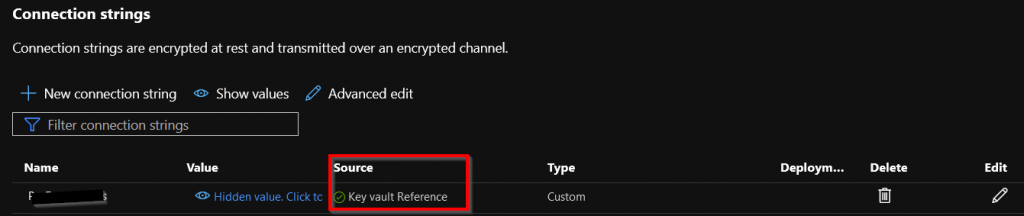
While this works very well, there is also a codeless way to access secrets from KeyVault. This is where KeyVault References come in. KeyVault References can be used to retrieve App Service Configuration Settings from KeyVault. When using the default .NET Core configuration for settings from JSON files with Host.CreateDefaultBuilder(args), AppSettings will be overwritten by any environment variable set with the same name as an AppSetting (see: https://docs.microsoft.com/en-us/aspnet/core/fundamentals/configuration/?view=aspnetcore-5.0). Since App Service Configure Settings are set as environment variables settings from JSON files appsettings.json can easily be overwritten when the application is deployed to App Service. If you have configured the App Service managed identity however, you can also overwrite your settings with secrets or keys from KeyVault. This can be done by referencing a KeyVault secret inside the App Setting, using a special KeyVault syntax. When this special syntax is used App Service will not use the App Setting value as is, but instead retrieve the value from KeyVault.
Referencing a value from KeyVault in an App Setting is as easy as using this syntax: “@Microsoft.KeyVault(SecretUri=https://myvault.vault.azure.net/secrets/mysecret/ec96f02080254f109c51a1f14cdb1931)” (quotes not included!). As you see here the secret version must be included for this to work. I found it easiest to copy the full URI from KeyVault by clicking on the secret and then clicking the secret version:
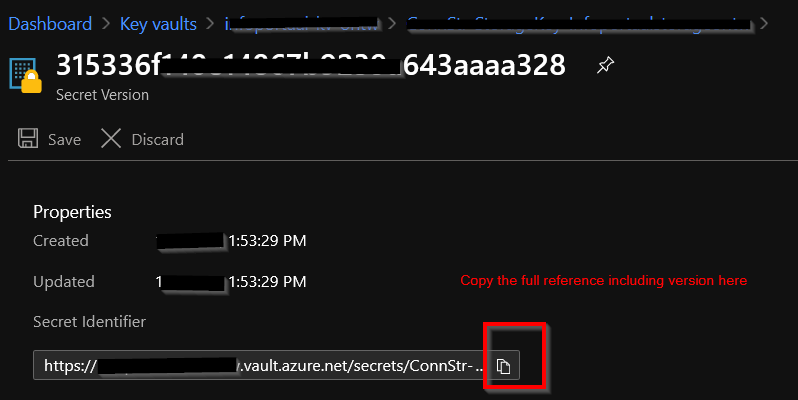
Place the URI in the special syntax: @Microsoft.KeyVault(SecretUri=) and copy the string in the App Service configuration setting to complete the reference to KeyVault. App Service will automatically validate the reference using the managed identity after saving the setting and you should be able to see the green checkmark if done correctly. Remember to set the KeyVault access policy first using the managed identity. The resulting setting should look like this in App Service: